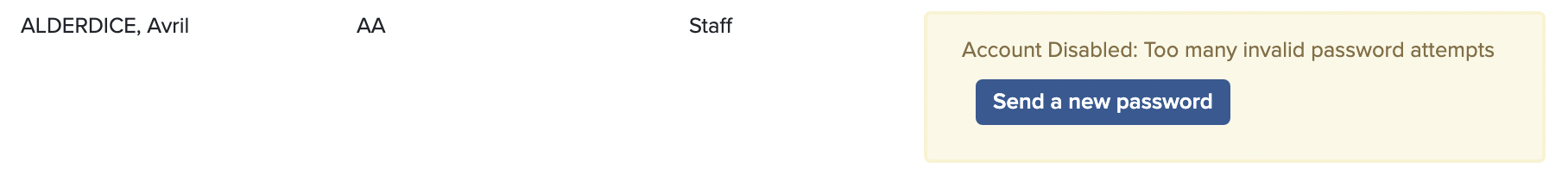Feb 8, 2024
We have four different authentication methods: SAML, LDAP, User/Password, LocalAuthentication.
- SAML: This is our preferred option and the one that works best for schools. It means each staff member only has to remember a single username and password which they use to log into their primary authentication system, and then every other application recognises the logged in user. This is more commonly called SSO or Single Sign On. This provides the best security where usernames and passwords are stored in a single – central – secure location.
- LDAP: Similar to SAML in the usernames and passwords are stored in a single location, however each application sees the username and password and therefore the secure aspect of LDAP is somewhat compromised.
- User / Password: The usernames and passwords are stored within each application. The staff member can end up with multiple different usernames and passwords for use with each of the applications they use. This is not ideal as in this situation staff often write down the username and passwords in order to remember them.
- LocalAuthentication is similar to SAML however it only works when used within the Windows network (it doesn’t work from home).
While our preference is a SAML authentication we still have a number of schools using the User/Password authentication process.
Recording invalid password attempts
When using (3) the Username / Password authentication process the staff member will often have the web browser remember the username and password to access SOBS. This is very useful and remains quite secure so long as the logged in device is secure. If a staff member changes their password without updating the web browser, then you may be in a situation where your password is not valid, and the application replies with an appropriate message.
One of the main changes staff will see is that there is now a count of remaining attempts on this message:
We have currently set this to allow 10 password attempts, after which the user account will be suspended for 30 minutes. When the 30 minute suspension period is finished the count is reset and the user can retry their login.
Why do we suspend the account?
If a hacker is aware of your username but not your password, they might try a “brute force” attack, which simply means trying to login using various random passwords. By counting the invalid password attempts, and then suspending the account for 30 minutes we are making it more difficult for hackers to break into your account – essentially they are limited to trying 20 different passwords each hour.
What do I do if my account is suspended?
When you attempt to login you will see a message like this:

Even if you were to login with the correct password, you will see this same message.
However, if you click the “Forgot password” link and reset your password, you will be able to login using the new password assigned.
Also, your SOBS Administrator will be able to see in the Staff List that your account is suspended, like this:
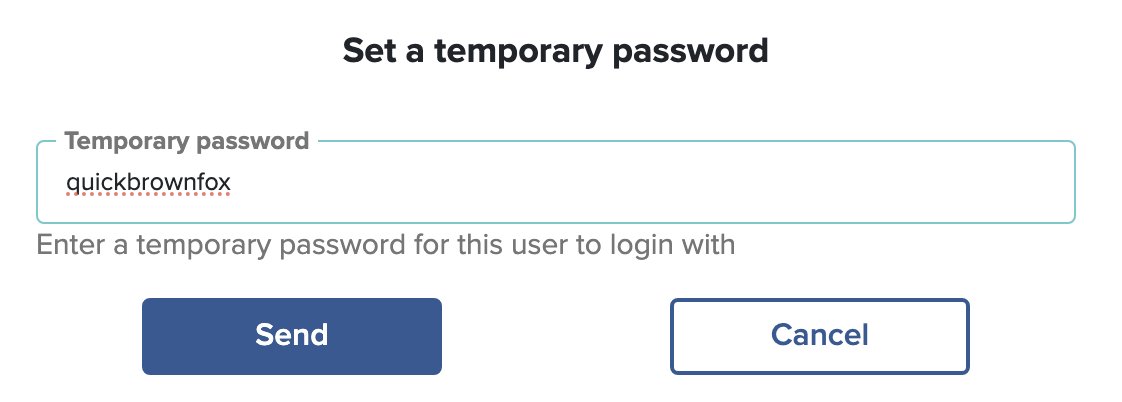
If the SOBS Administrator clicks on the button “Send a new password” they will be prompted to enter a temporary password, which will be set on the staff record and emailed to the staff member.